Wireshark
Display filters, TLS inspection, and practical workflow
Wireshark uses display filters to quickly find relevant network traffic. Below are common filters and a practical method to decrypt TLS traffic in your own browser session.
Common display filters
HTTP, HTTPS, and ports
-
HTTP traffic (port 80)
tcp.port == 80 -
HTTPS traffic (port 443)
tcp.port == 443 -
Any TCP traffic on a specific port
tcp.port == 12345 -
Show only GET requests
http.request.method == "GET" -
Show only POST requests
http.request.method == "POST" -
Only traffic to a specific HTTP host header
http.host == "host.example.com" -
TLS handshakes (ClientHello)
tls.handshake.type == 1This is very useful to identify domains via SNI during TLS setup.
Decrypting TLS traffic (SSLKEYLOGFILE)
Inspect HTTPS content for your own browser session
To decrypt TLS traffic, you can configure browsers like Firefox (and Chromium-based browsers) to write session keys to a file. Wireshark can use that file to decrypt the captured TLS streams.
Security note: the key log file allows decrypting captured TLS traffic for those sessions. Treat it as sensitive and delete it when done.
Windows
-
Create a user environment variable
Variable name: SSLKEYLOGFILE Variable value: %USERPROFILE%\AppData\Local\Temp\sslkeylog.logAfter setting the variable, restart your browser.
Linux
-
Export SSLKEYLOGFILE (per session)
export SSLKEYLOGFILE="$HOME/ssl-key.log" touch "$HOME/ssl-key.log" chmod 600 "$HOME/ssl-key.log"Start Firefox from the same terminal, and keep other browsers closed for clarity.
Configure Wireshark to use the key log
-
Load the SSL/TLS key log file
Edit > Preferences > Protocols > TLS (Pre)-Master-Secret log filename: browse to your ssl-key.log
Improving the Wireshark view
Columns, timestamps, and useful fields
-
Hide columns
Right-click a column header > uncheck columns you do not need (e.g. "No." or "Length"). -
Remove columns
Right-click a column header > "Remove this Column" -
Add columns for Source Port and Destination Port
Right-click a column header > "Column Preferences..." Click "+" to add a column Set type: Src port (unresolved) Add another: Dest port (unresolved) -
Change time display to UTC
View > Time Display Format > UTC Date and Time of Day View > Time Display Format > Seconds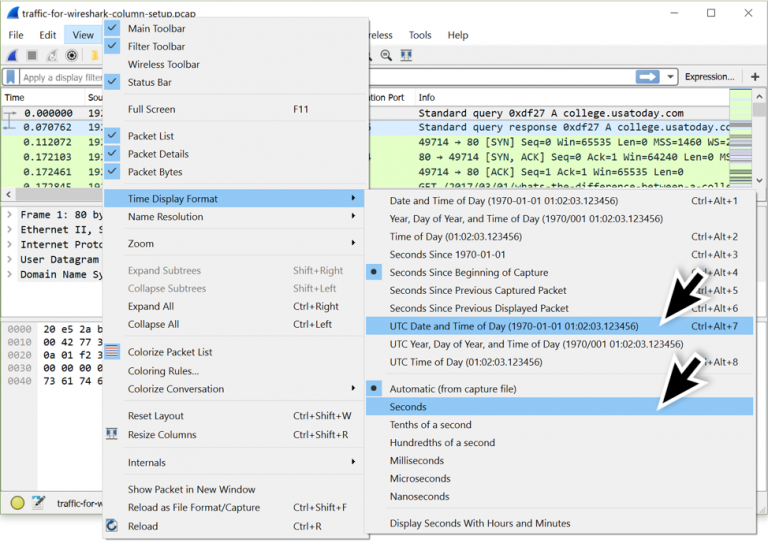
Quick domain identification
HTTP Host and TLS SNI (Server Name Indication)
If you want to quickly identify domains in traffic:
-
HTTP domains (Host header)
Filter: http.requestExpand: Hypertext Transfer Protocol Select: Host: ... Right-click > Apply as Column -
HTTPS domains (TLS SNI)
Filter: tls.handshake.type == 1Expand: Transport Layer Security Expand: Handshake Protocol: Client Hello Expand: Extension: server_name Select: Server Name: ... Right-click > Apply as Column
With this customization, you can filter quickly on http.request or tls.handshake.type == 1
and still see the destination domains as a column.
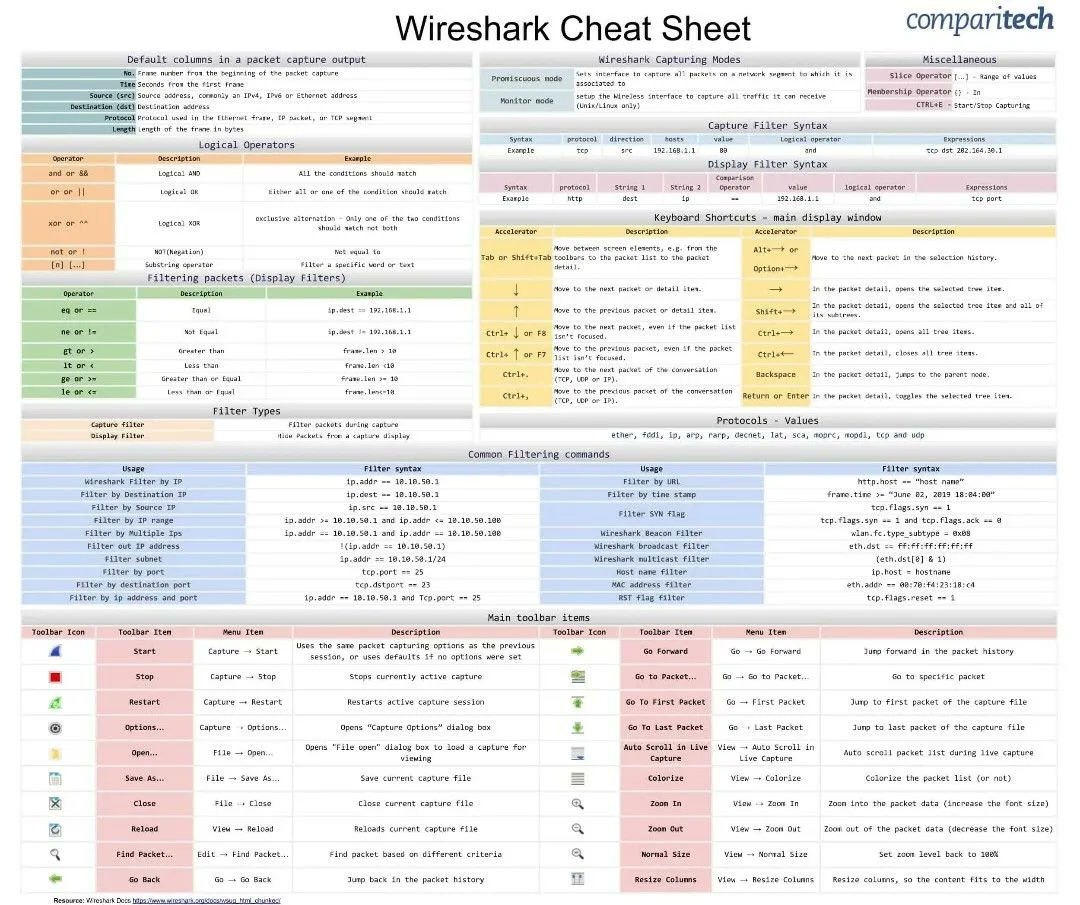
Wireshark cheat sheet