SSH Hardening
How to harden your SSH server
-
On the client
ssh-keygen -t ed25519 -a 420 -f ~/.ssh/demo.ed25519 -C "mykey for demo"
cat ~/.ssh/demo.ed25519.pub
Copy and then upload public key to the server
Create a config file on the client
vi ~/.ssh/config
Host shortname for server
Hostname fqdn.example.com
User login user
Port port to use
PreferredAuthentications publickey
IdentityFile~/.ssh/demo.ed25519
On the server
mkdir ~/.ssh; touch ~/.ssh/authorized_keys; chmod 700 ~/.ssh
vi ~/.ssh/authorized_keys
paste here the client key
chmod 400 ~/.ssh/authorized_keys
SSH configuration
vi /etc/ssh/sshd_conf
Port 22
ListenAddress 0.0.0.0
ListenAddress ::
Protocol 2
HostKey /etc/ssh/ssh_host_ed25519_key
HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
# Specifies the ciphers allowed
Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr
#Ciphers aes256-ctr,aes192-ctr,aes128-ctr
#Specifies the available MAC (message authentication code) algorithms
MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-512,hmac-sha2-256,umac-128@openssh.com
SyslogFacility AUTH
LogLevel VERBOSE
# Log sftp level file access (read/write/etc.) that would not be easily logged otherwise.
Subsystem sftp /usr/lib/ssh/sftp-server -f AUTHPRIV -l INFO
LoginGraceTime 2m
PermitRootLogin no
PasswordAuthentication no
StrictModes yes
PubkeyAuthentication yes
HostbasedAuthentication no
PermitEmptyPasswords no
ChallengeResponseAuthentication no
UsePAM no
AllowTcpForwarding yes
X11Forwarding yes
X11DisplayOffset 10
PrintMotd no
PrintLastLog yes
TCPKeepAlive yes
Compression yes
ClientAliveInterval 15
ClientAliveCountMax 3
UseDNS no
chown root:root /etc/ssh/sshd_config
chmod 600 /etc/ssh/sshd_config
Remove the passphrase for existing the SSH key
ssh-keygen -p -f name-of-private-key
Change the comment field of an existing SSH key
ssh-keygen -f ~/.ssh/mykey -c -C 'a new comment' -o
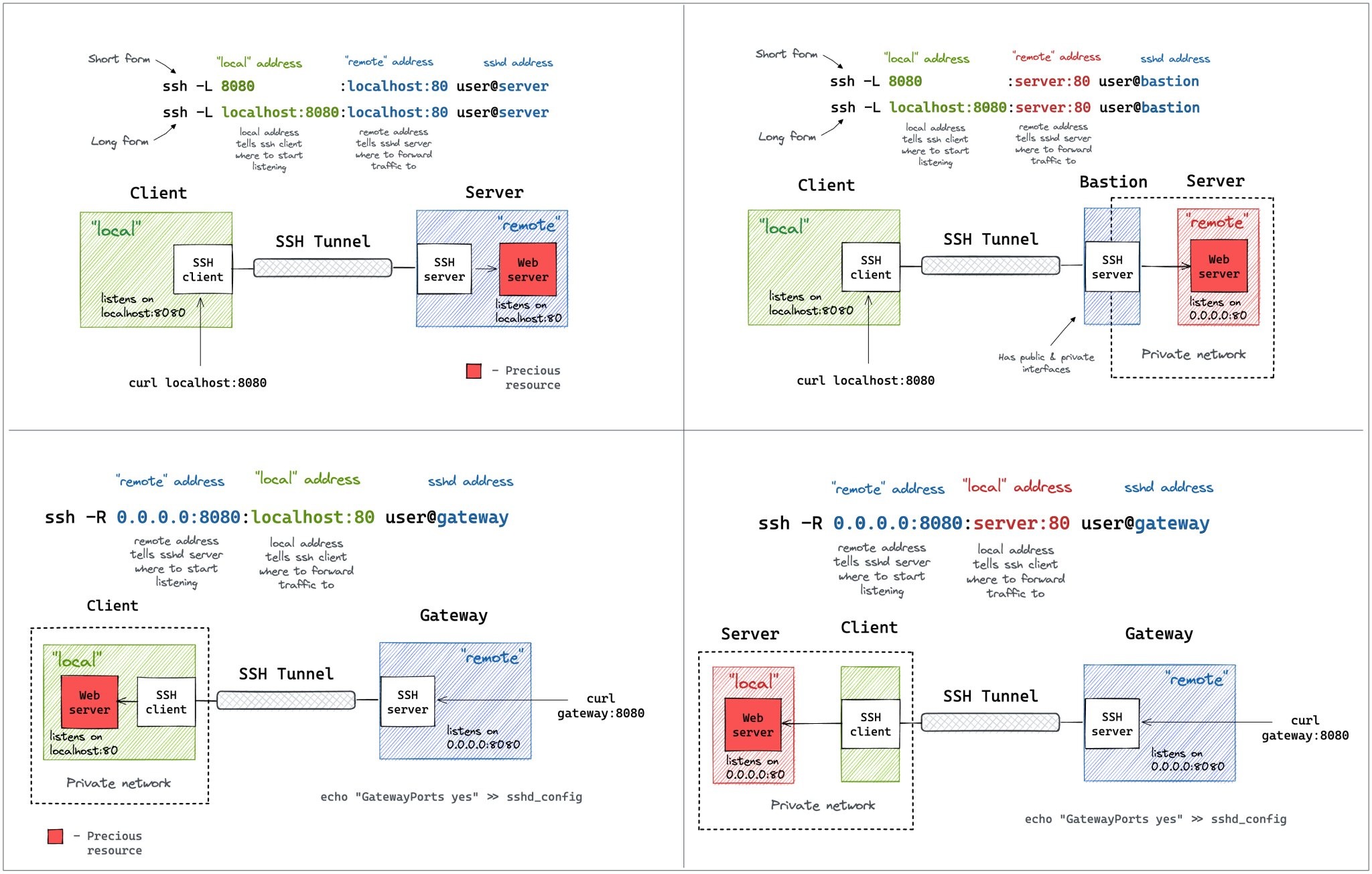
SSH Tunneling
ssh-keygen -L